How to create a GPG key pair? How to publish a GPG public key? Here is a short and handy guide 🙂
PGP: stands for Pretty Good Privacy and it was created by Symantec
GPG: stands for GNU Privacy Guard, an alternative to Symantec’s official PGP software
First of all install and test it:
$ sudo apt install pgpgpg
$ gpg --list-keys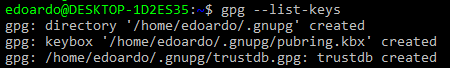
Let’s now create our keys running the wizard and filling the requested information:
$ gpg --full-gen-key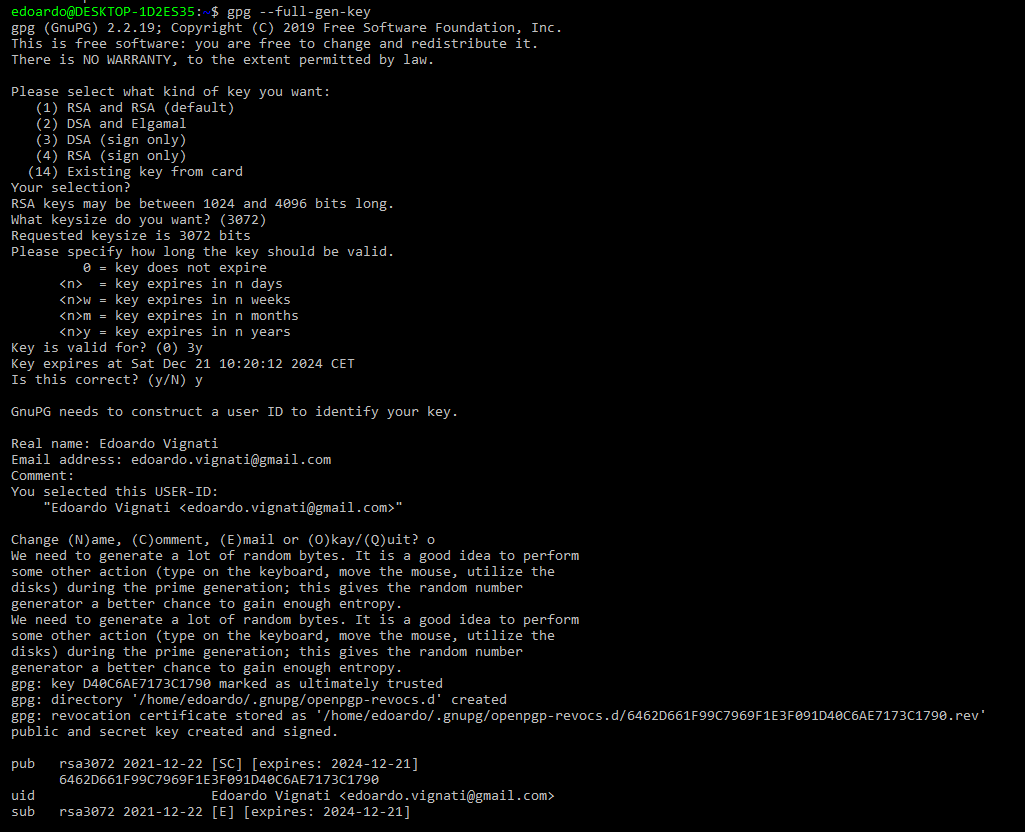
During the keys generation, you will be asked to insert your secret passphrase, DO NOT lose it.
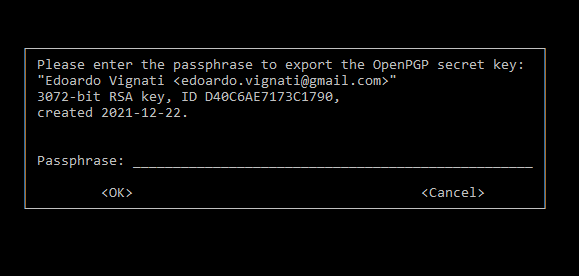
Generate now the revocation certificate in case something happens such as your private key is compromised:
$ gpg --output revoke.asc --gen-revoke <[email protected]>Store the output file in a safe place (a pendrive or print it).
Now we are ready to deploy our public key on a key server.
Export the PUBLIC key with the following command:
$ gpg --output public.pgp --armor --export <[email protected]>You can now upload the PUBLIC key file, for example, at the Symantec server: keyserver.pgp.com
With this last command we export the PRIVATE key that MUST NOT be shared with anyone:
gpg --output private.pgp --armor --export-secret-key <[email protected]>Cheers!

 This work is licensed under a
Creative Commons Attribution-NonCommercial 4.0 International License.
This work is licensed under a
Creative Commons Attribution-NonCommercial 4.0 International License.
